Generate Private Key From Pem File Online
- Generate Private Key From Pem File Online Login
- Generate Private Key From Pem File Online Application
- Windows Generate Pem File
- Private Key Pem File
- Generate Private Key From Pem
When you are working with JAVA applications and JAVA based server, you may need to configure a Java key store (JKS) file. Self signed keystore can be easily created with keytool command. But if you have a private key and a CA signedcertificate of it, You can not create a key store with just one keytool command.
You need to go through following to get it done.
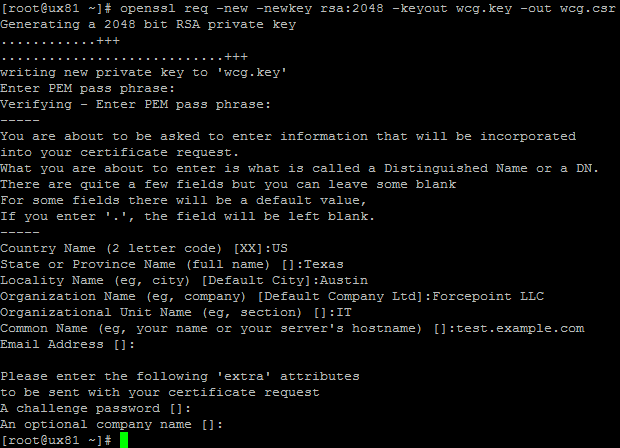
Step 1. Create PKCS 12 file using your private key and CA signed certificate of it. You can use openssl command for this.
If your private key has a password, It would promote to enter the password of private key. You need to define a password for PKCS 12 file as well.
- I needed to generate a new private key and then import the updated certificate from the certificate provider. If the private key doesn't exist on your computer then you can't export the certificate as pfx. They option is greyed out.
- Ssh-keygen -t ecdsa -b 521 -C 'ECDSA 521 bit Keys' Generate an ed25519 SSH keypair- this is a new algorithm added in OpenSSH. Ssh-keygen -t ed25519 Extracting the public key from an RSA keypair. Openssl rsa -pubout -in privatekey.pem -out publickey.pem Extracting the public key.
- Just as a.crt file is in.pem format, a.key file is also stored in.pem format. Assuming that the cert is the only thing in the.crt file (there may be root certs in there), you can just change the name to.pem. The same goes for a.key file. Which means of course that you can rename the.pem file to.key.
As an example, say i have a private key called “server.pem” and certificate with “servercret.pem”
When you are working with JAVA applications and JAVA based server, you may need to configure a Java key store (JKS) file.Self signed keystore can be easily created with keytool command. But if you have a private key and a CA signed certificate of it, You can not create a key store with just one keytool command. You need to go through following to get it done. Inspecting the output file, in this case privateunencrypted.pem clearly shows that the key is a RSA private key as it starts with -BEGIN RSA PRIVATE KEY-. Visually Inspect Your Key Files. It is important to visually inspect you private and public key files to make sure that they are what you expect.
Step 2. Create JKS file using keytool command
Generate Private Key From Pem File Online Login
Created PKCS 12 file has been given as the source keystore and new file name (wso2carbon.jks) has been given as the destination keystore.
Generate Private Key From Pem File Online Application
As an example,
As an additional steps, you can change the private key password of the created JKS file and also the alias name for your private key entry.
Step 3 (Optional). Changing the password of private key file in keystore. More details from here as well
Step 4 (Optional). Change the alias name of the private key entry
By default [current alias] is set to “1”
Windows Generate Pem File
Thanks for reading…!!! Also you can find more details on creating self signed KeyStore from here
Related posts:
.pem SSL Creation Instructions
SSL .pem files (concatenated certificate container files), are frequently required for certificate installations when multiple certificates are being imported as one file.
This article contains multiple sets of instructions that walk through various .pem file creation scenarios.
Creating a .pem with the Entire SSL Certificate Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt), Root (TrustedRoot.crt), and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.

Creating a .pem with the Server and Intermediate Certificates
Private Key Pem File
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Private Key and Entire Trust Chain
Generate Private Key From Pem
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Private Key - your_domain_name.key
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN RSA PRIVATE KEY-----
(Your Private Key: your_domain_name.key)
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.