Mac Os X Generate Pgp Keys
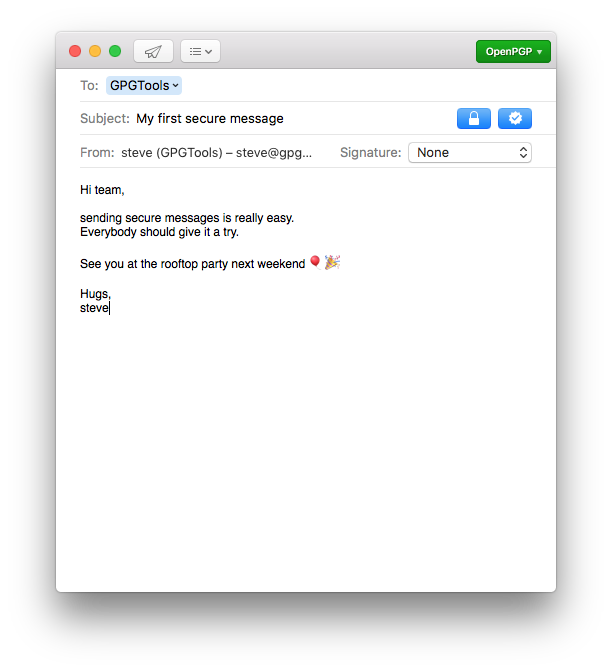
PThis article details how to create PGP keys in Encryption Desktop (previously PGP Desktop) for Mac OS X.p PGP Keys are essential to the use of Encryption Desktop encryption, therefore it is important to backup your keys by either exporting the key(s) to a file and storing in a secure location. I looked into dozens of ways to set up PGP on my Mac. A lot of them suck for a plurality of reasons. Across the board, this is the best way for 95% of use cases. Step 1: Install the GPGTools GPG Suite for OS X. This step is simple. Visit the GPGTools website and download the GPG Suite for OS X. Once downloaded, mount the DMG and run the 'Install'. Use PGP Desktop to create PGP keypairs and manage both your personal keypairs and the public keys of others. To make the most of PGP Desktop, you should be familiar with PGP Desktop Terminology Desktop for Mac OS X.

Mac Os X Generate Pgp Keys Free
Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. It was created by Phil Zimmermann in 1991. PGP and similar software follow the OpenPGP standard (RFC 4880) for encrypting and decrypting data. Source: Wikipedia
This site only provides a simple, safer and easy-to-use tool for people who want to generate a pair of PGP keys or more. Today, some common methods for generating keys still involve going to a command prompt of a Linux/Unix machine and using the GPG utility, or installing a PGP compatible application on your desktop, so I wanted to provide an easier way to generate keys. None of this would be possible without the awesome open source software that I'm using which is KeyBase's awesome JavaScript implementation of PGP (kbpgp). While for file saving capabilities, I am using Eli Grey's wonderful FileSaver.js interface.
This site is open source and the source code are available on GitHub under MIT License. If you have any inquiry or problem, you may create an issue here.
This guide will demonstrate the steps required to encrypt and decrypt files using OpenSSL on Mac OS X. The working assumption is that by demonstrating how to encrypt a file with your own public key, you'll also be able to encrypt a file you plan to send to somebody else using their private key, though you may wish to use this approach to keep archived data safe from prying eyes.
Too Long, Didn't Read
Assuming you've already done the setup described later in this document, that id_rsa.pub.pcks8 is the public key you want to use, that id_rsa is the private key the recipient will use, and secret.txt is the data you want to transmit…
Encrypting
Decrypting
Using Passwords
OpenSSL makes it easy to encrypt/decrypt files using a passphrase. Unfortunately, pass phrases are usually 'terrible' and difficult to manage and distribute securely.
To Encrypt a File
You can add -base64 if you expect the context of the text may be subject to being 'visible' to people (e.g., you're printing the message on a pbulic forum). If you do, you'll need to add it to the decoding step as well. You can choose from several cypers but aes-256-cbc is reasonably fast, strong, and widely supported. Base64 will increase the size of the encrypted file by approximately 30%
To Decrypt a File
You will need to provide the same password used to encrypt the file. All that changes between the encrypt and decrypt phases is the input/output file and the addition of the -d flag. If you pass an incorrect password or cypher then an error will be displayed.
Encrypting Files Using your RSA keys
RSA encryption can only work with very short sections of data (e.g. an SHA1 hash of a file, or a password) and cannot be used to encrypt a large file. The solution is to generate a strong random password, use that password to encrypt the file with AES-256 in CBC mode (as above), then encrypt that password with a public RSA key. The encrypted password will only decrypt with a matching public key, and the encrypted file will require the unique password encrypted in the by the RSA key.
Replace OpenSSL
The copy of OpenSSL bundled with Mac OS X has several issues. Mac OS X 10.7 and earlier are not PCI compliant. It is best to replace it. See here for details: http://www.dctrwatson.com/2013/07/how-to-update-openssh-on-mac-os-x/
Generate Your Private/Public Key-pair
By default your private key will be stored in Nexus 3000 generate rsa key.
- ~/.ssh/id_rsa : This is your private key and it must be kept secret
- ~/.ssh/id_rsa.pub : This is your public key, you can share it (for example) with servers as an authorized key for your account.You can change the location of where you store your keys, but this location is typical. Typically you want to ensure the private key is chmod 600, andd the public key is chmod 644.
Generate a PKCS8 Version of Your Public Key
The default format of id_rsa.pub isn't particularly friendly. If you are going to public your key (for example) on your website so that other people can verify the authorship of files attributed to you then you'll want to distribute it in another format. I find it useful to keep a copy in my .ssh folder so I don't have to re-generate it, but you can store it anywhere you like.
Generate a One-Time-Use Password to Encrypt the File
The passwords used to encrypt files should be reasonably long 32+ characters, random, and never used twice. To do this we'll generate a random password which we will use to encrypt the file.
This will generate 192 bytes of random data which we will use as a key. If you think a person may need to view the contents of the key (e.g., they're going to display it on a terminal or copy/paste it between computers) then you should consider base-64 encoding it, however:
- The password will become approximately 30% longer (and there is a limit to the length of data we can RSA-encrypt using your public key
- The password will be 'padded' with '=' characters if it's not a multiple of 4 bytes.
A Note on Long Passwords
Create Pgp Keys
There is a limit to the maximum length of a message that can be encrypted using RSA public key encryption. If you want to use very long keys then you'll have to split it into several short messages, encrypt them independently, and then concatinate them into a single long string. Decrypting the password will require reversing the technique: splitting the file into smaller chuncks, decrypting them independently, and then concatinating those into the original password key file.
Encrypt the File Using the Generated Key
Now that you have a good random password, you can use that to AES encrypt a file as seen in the 'with passwords' section
Decrypting the file works the same way as the 'with passwords' section, except you'll have to pass the key.
Encrypt the Key Used to Encrypt the File
We used fast symetric encryption with a very strong password to encrypt the file to avoid limitations in how we can use asymetric encryption. Finally, we'll use asymetric encryption to encrypt the password. This solves the problem of 'how do I safely transmit the password for the encrypted file' problem. You can encrypt is using the recipients public key and they can decode it using their private key. Encrypt the password using a public key:
The recipient can decode the password using a matching private key:
Package the Encrypted File and Key
There are a number of ways to do this step, but typically you'll want just a single file you can send to the recipent to make transfer less of a pain. I'd recommend just making a tarball and delivering it through normal methods (email, sftp, dropbox, whatever). Though a secure method of exchange is obviously preferable, if you have to make the data public it should still be resistent to attempts to recover the information.
The file can be extracted in the usual way:
You may want to securely delete the unecrypted keyfile as the recipient will be able to decode it using their private key and you already have the unencrypted data.